


From complex security applications to real-time visibility
AI-powered control analysis and decision support for Cybersecurity and Compliance
You've built a sophisticated security stack...
And yet answering "Are we secure?" still takes longer than planned.
You've invested in the best SIEM for threat detection, EDR for endpoint protection, vulnerability scanners for risk assessment, GRC platforms for compliance tracking. Each tool excellent at its job, each generating critical data.
But when the board asks that fundamental question: "Are we secure and compliant?", you're still pulling reports from different sources. Your tools are world-class. The integration between them doesn't exist.
This fragmentation isn't just inconvenient - it's expensive.
Every uncontrolled tool compounds the operational chaos and cost. Your team chases evidence across systems while real threats evolve. The board demands answers you can't provide fast enough.
Cost savings from extensive use of AI in security, compared to organizations that didn’t use these solutions (IBM)
The global average cost of a data breach, a 9% decrease over last year - driven by faster identification and containment (IBM)
Share of organizations that reported an AI-related security incident and lacked proper AI access controls (IBM)
Imagine walking into Monday's board meeting with complete confidence
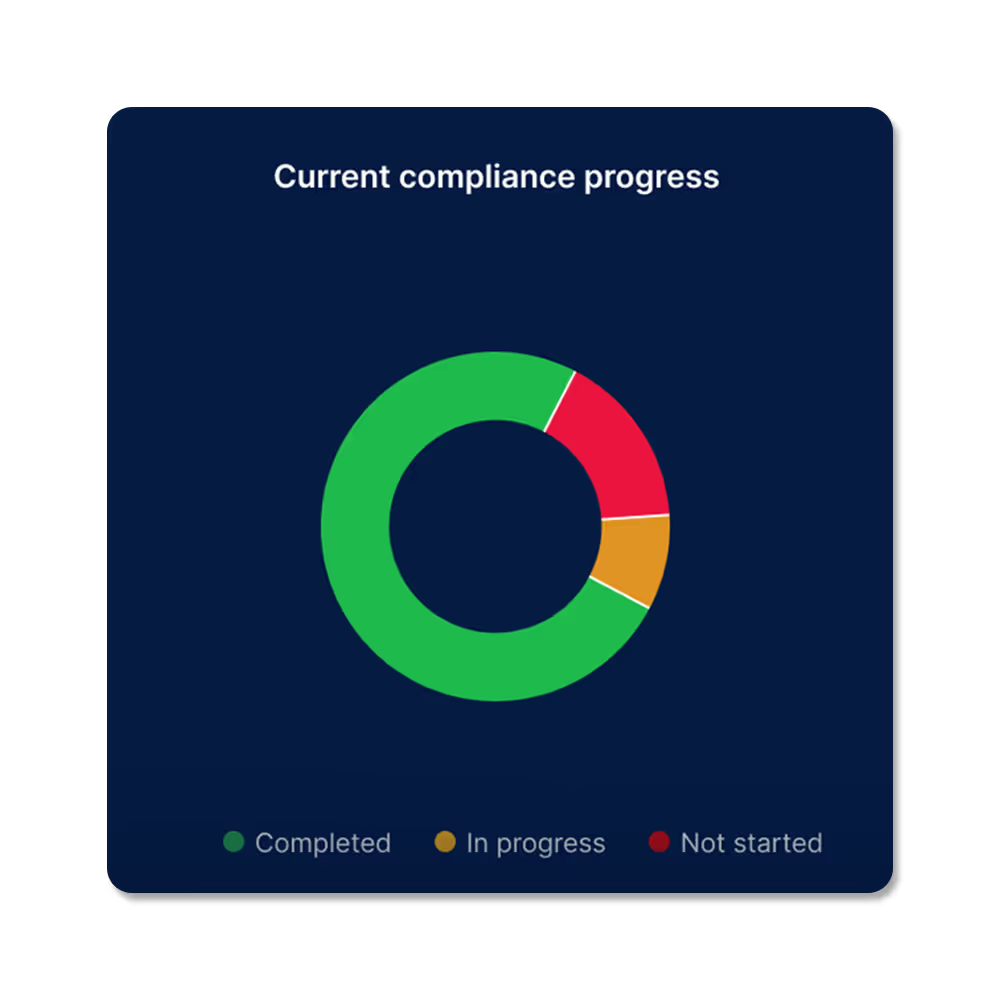
Live Team Data
Your team focuses on strengthening security instead of chasing evidence across many tools. When the board asks "Are we secure?", you answer with live data, not last week's PowerPoint. Deals close faster because you demonstrate compliance in minutes, not weeks.
Centralized Command
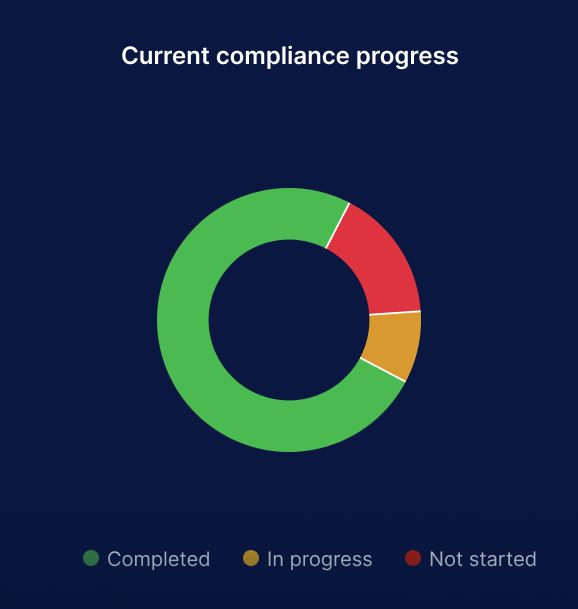
One dashboard showing your entire security posture across CIS and ISO 27001 controls. Every control tracked. Every gap visible. Every improvement measurable in real-time with AI.
Full Transparency
This isn't about adding another tool. It's about finally having unified visibility over everything you've built
No rip-and-replace. Just unified control.
Compliance transformed from complex puzzle to clear strategy. SecuraTrack turns technical controls into business language that makes sense.
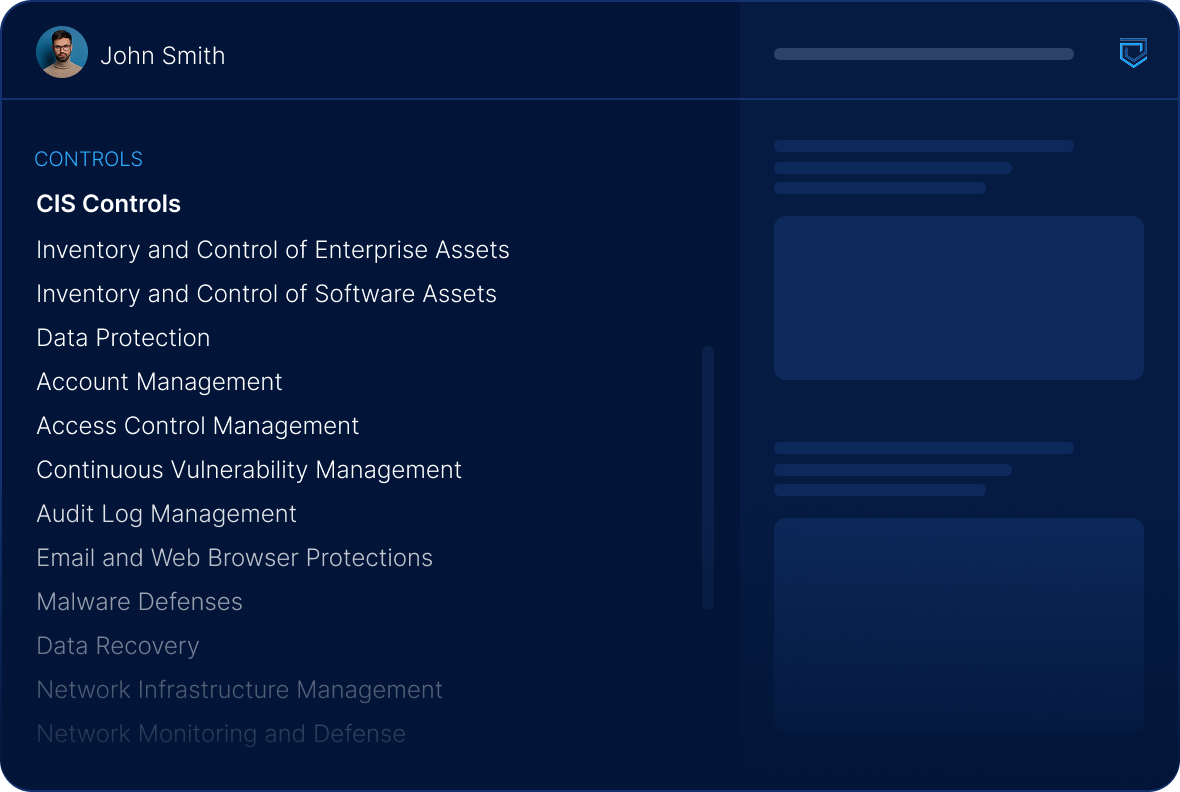
Unified control mapping
We map your existing controls across NIST, ISO, CIS, DORA, NIS2, and CMMC into one unified framework.
Everything Together
We connect your security tools through our orchestration layer—keeping everything you've built
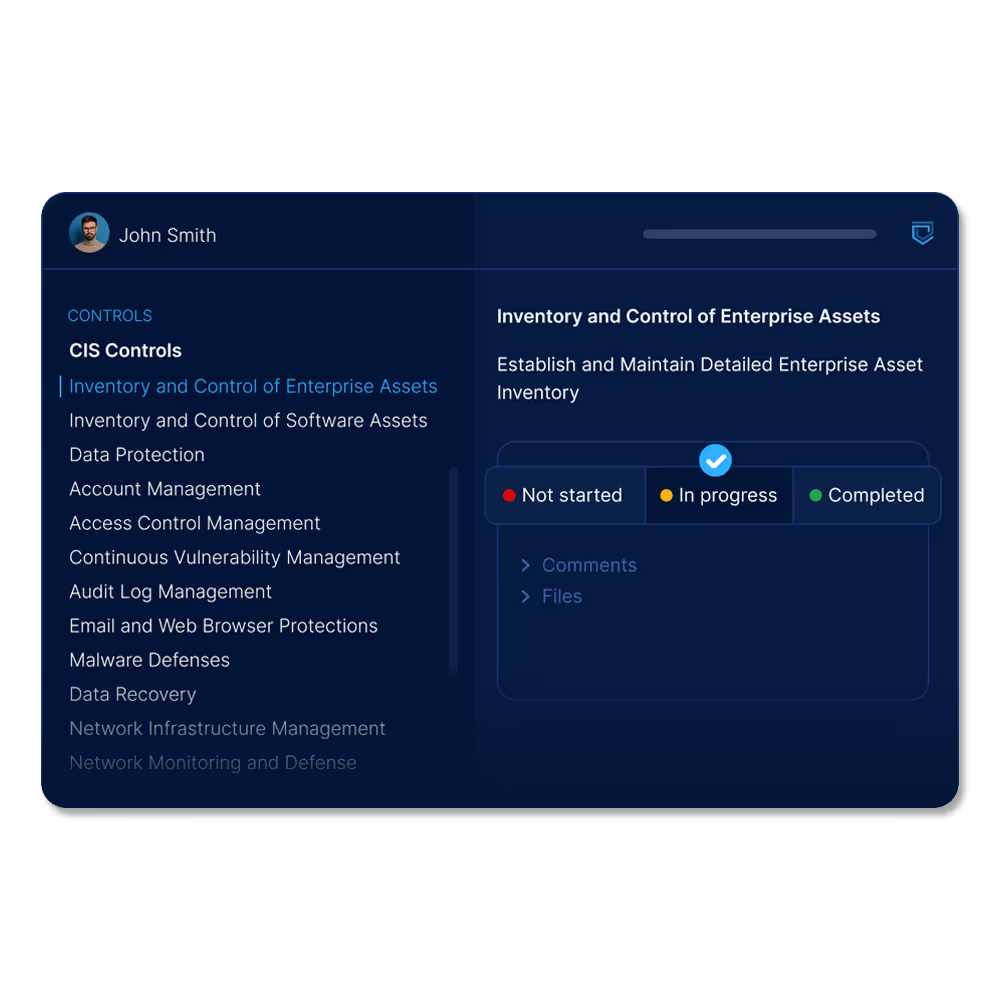
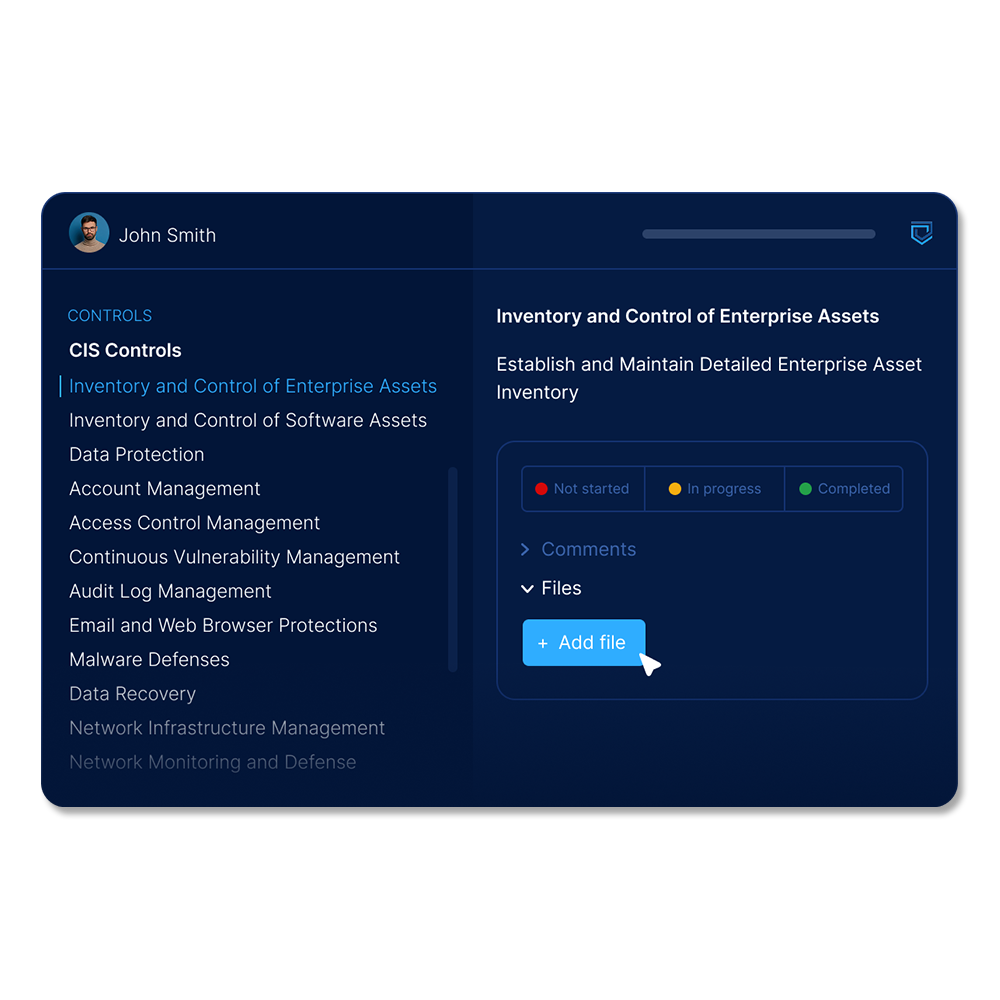
Automated evidence collection
We automate evidence collection across your entire environment, eliminating manual gathering
Only The Data You Need
We build executive dashboards that answer any security question with live data
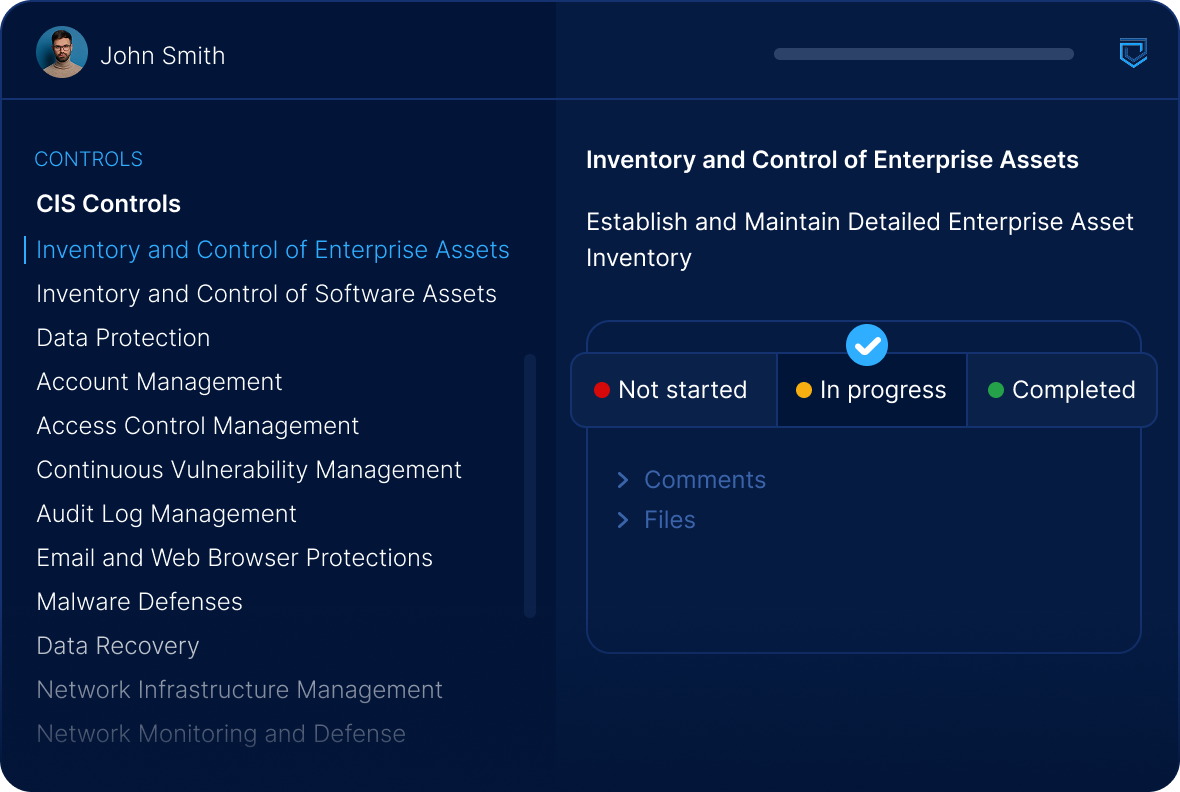
Simplify Complexity
We establish continuous compliance monitoring while your team focuses on security improvements
Stop proving.
Start improving.
Join security leaders who've moved from PowerPoint chaos to unified command. No credit card required. No complex setup. Just instant visibility into your entire security program.
What CISOs ask about SecuraTrack.
Complete platform access for 90 days. Track 500+ controls across multiple frameworks with zero financial commitment. No credit card required.
No. We integrate with your current security infrastructure. Think of us as a translator that connects your existing tools, not a replacement.
Rapid deployment means full platform integration within 10 weeks. We map controls in two weeks, connect tools by week four, and have executive dashboards running shortly after.
Complete platform access for 90 days. Track 500+ controls across multiple frameworks with zero financial commitment. No credit card required.
